Overview of Yaad's Security
Ali Khaleqi Yekta•
Tech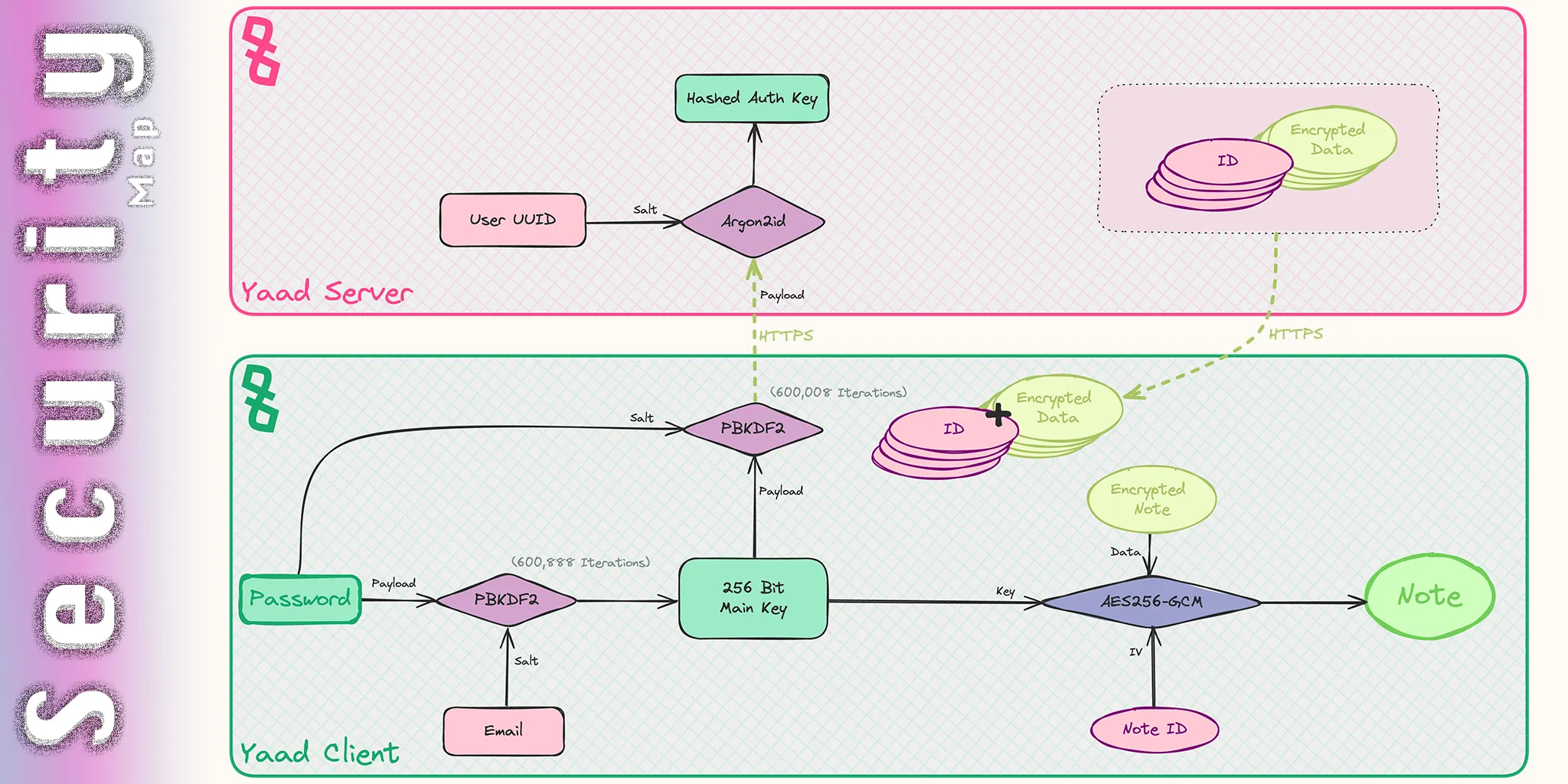
Yaad takes security seriously. Being able to have a trusted place to store everything with no worries is one of the main reasons Yaad was created in the first place. Going straight to the point, the image you see above is the high-level map of how Yaad ensures the security of your data. In the case of this map, it's particularly describing the decryption process of a single note. It is conceptually similar to the approach taken by most password managers. Let's break it down:
Password: The first line of defense, and the most vulnerable part of the entire process is the password you enter upon signing up. This password is used to derive the Main Key, which is later used to encrypt and decrypt your data. By choosing a strong password, and having it in a password manager or remembering it, your account will be in its most secure state, and you can rest assured that your data is safe. The password you enter will never leave your device.
Main Key: The Main key is derived from your Password, using the PBKDF2 key derivation function, with 600,888 iterations and a 256-bit key length. Your email is the salt in this process. The main key is used to encrypt and decrypt your data. This key also never leaves your device and is derived locally on your device, upon opening the app.
Auth Key: The Auth key is derived from the Main Key, again using the PBKDF2 key derivation function, with 600,008 iterations and a 256-bit key length. Your original password is the salt in this process. This key is then sent to the server and used to derive the Auth Key. It is hashed using the Argon2id password hashing function, using the User UUID as the salt. The result is stored in the database and is known as the Auth Key, which is used to identify you on your future logins. This is the only key that leaves your device. Since the actual password, and hence the Main Key, cannot be "recovered" from the Auth Key, no one can access the actual information within your encrypted data on the server, even if all the servers' data is compromised.
Data Encryption: The content of all of your entities (notes, tasks, people), your note histories, your boxes, and the links between your entities are encrypted using the AES-256-GCM encryption algorithm. The Main Key is the encryption key, and each item's UUID is its IV for the encryption. The encryption is done locally on your device. The encrypted data is then sent to the server, where it is stored.
This is a high-level overview of how Yaad ensures the security of your data. If you have any questions, feel free to email the support at [email protected].